Despite the Snowden revelations of the extent of official data gathering and storage on individuals, the overwhelming majority of citizens have not only resigned themselves to electronic surveillance but are putting themselves in a position to have their habits examined microscopically by bringing eavesdropping digital assistants into their home and buying “smart” home appliances.
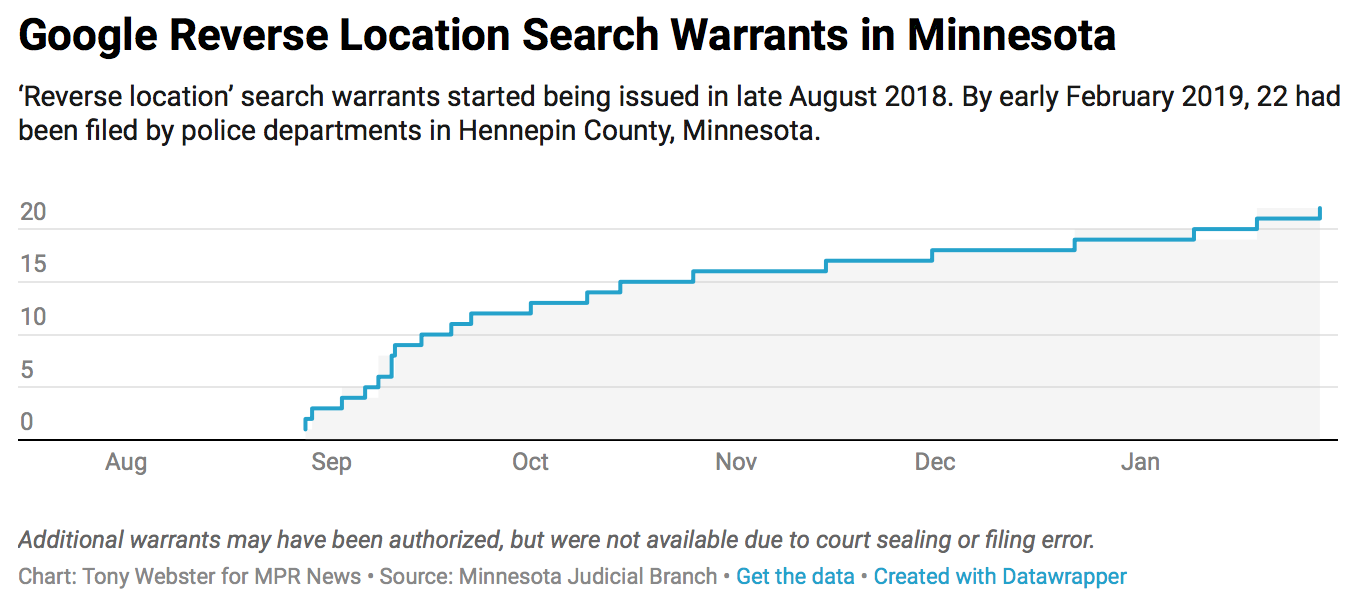
Nevertheless, for those of you who care about your civil liberties, a new form of police digital information collection, known as a “reverse location search warrant” have been approved by courts in Maine, Minnesota, North Carolina and Virginia, even though the ACLU contends that these search warrants violate the Fourth Amendment by not being sufficiently specific.
A “reverse location search warrant” is when the police seek information on all cell phones that have been near a crime scene. As we’ll discuss in more detail belwo concerns that these are data fishing expeditions appear valid when you look at how unnecessarily broad these search warrants have been, not only extending as much as a day before and after the incident, but also encompassing a large area. For instance, a story in MPR News (hat tip Chuck L) showed the extent of the search area relative to the crime location:
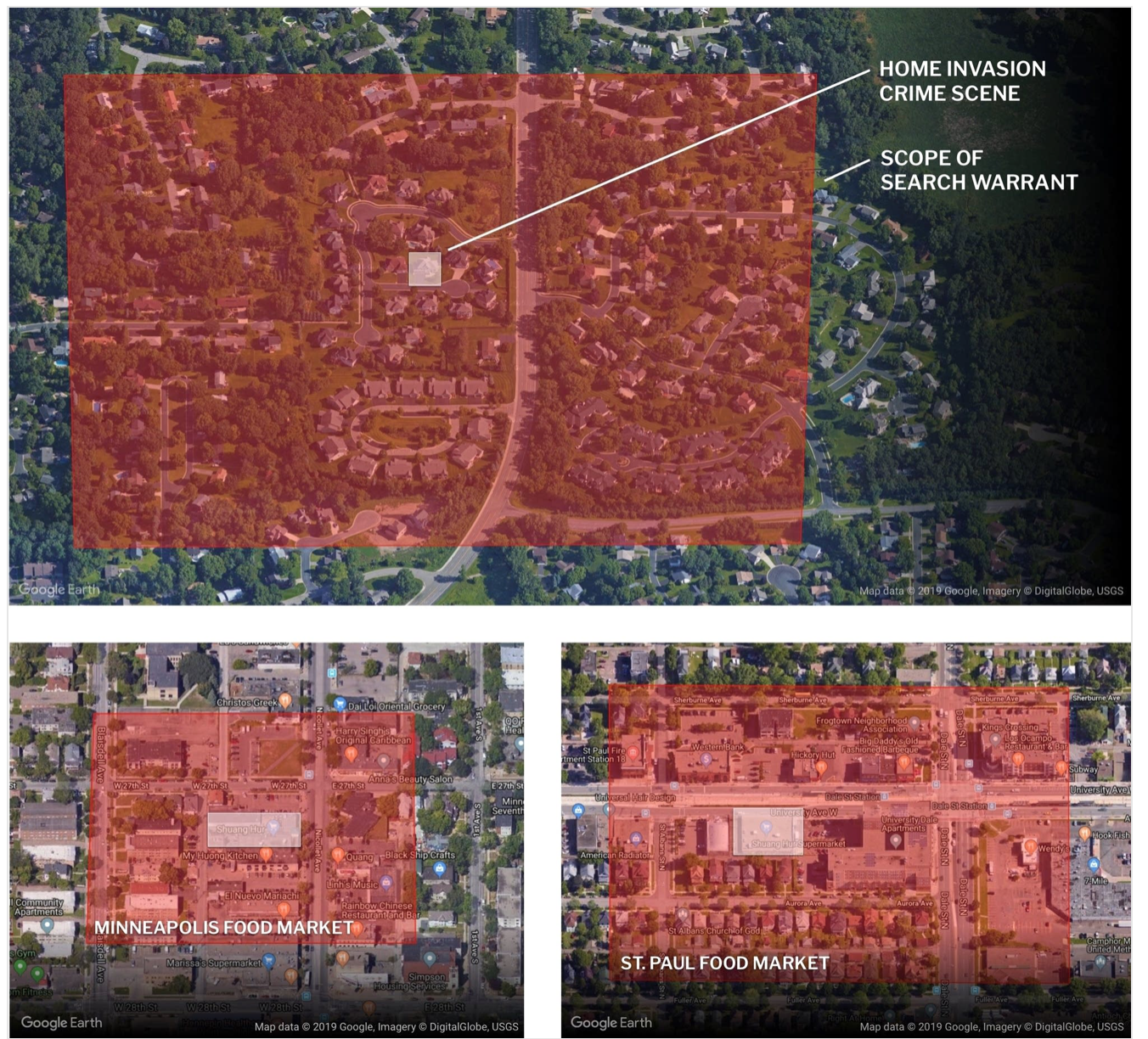
As the article pointed out:
The scope of the warrant was so expansive in time and geography that it had the potential to gather data on tens of thousands of Minnesotans.
And the police don’t have to go to different carriers and then have to integrate the information. This practice is made oh so much easier due to Google serving as one stop shopping. Again from the MPR News story:
“[A] high percentage of the population regularly carries and uses a cellular phone,” wrote a detective in one of these search warrant applications. “Google monitors its customers’ activities and location through its free apps and services in order to provide more timely responses to queries and for targeted advertising … [t]he services may be actively in use or running in the background on the device without the user’s knowledge.”
Google’s lengthy user agreement does specify that any data Google keeps may be provided to police in response to a legal demand. But the process by which a user consents to the data collection isn’t always clear….
Apple’s iOS and Google’s Android operating systems collect location information using built-in GPS chips, and by scanning for nearby Wi-Fi networks, cell towers, and Bluetooth signals to build a crowdsourced database of location information to help the devices quickly figure out where they are.
But while Apple’s location data processing is anonymous, two hard-to-find settings— “Location History” and “Web and App Activity” — allow Google to keep track of everything their users search, and everywhere they go. It affects all Android users, and iPhone or iPad users with apps like Google Maps installed on their device.
So if you have downloaded Google Maps (and Lord only knows what other apps), being on an Apple device won’t protect you.
And cops are keen to have access to this data. The police in Minnesota started using reverse location search warrants after they heard about their use in Maine, North Carolina, and Virginia, and they are seeking more with every passing month:
Now in theory this should quickly become self-correcting. Anyone perpetrating a planned crime will leave their device at home and if they really need a phone, will get a burner they dispose of (I thought serious crook like drug dealers did this already). But in practice, unless civil liberties groups can bar or severely restrict the use of these search warrants, their use is certain to rise regardless of how productive they prove to be…not just “because data” but because ZetX, a company that trains policemen in cellphone investigations, also sells software called TRAX that, per MPR News, “generates legal documents and maps cellphone data to assist in analysis.”
Fishing Expeditions as Search Warrants
Given how specific cell phone location data is (both the GPS location and the time stamping), the willingness of judges to sign off on search warrants that go well beyond the immediate time and site of a crime is troubling.
One of the first media discussion of these reverse location search warrants appears to have come in a Forbes article last year by cybersecurity reporter Thomas Brewster, shortly after a report by WRAL on reverse location search warrant use in North Carolina. From Forbes:
Back in March, as it investigated a spate of armed robberies across Portland, Maine, the FBI made an astonishing, unprecedented request of Google. The feds wanted the tech giant to find all users of its services who’d been within the vicinity of at least two of nine of those robberies. They limited the search to within 30-minute timeframes around when the crimes were committed. But the request covered a total space of 45 hectares and could’ve included anyone with an Android or iPhone using Google’s tools, not just the suspect.
The FBI then demanded a lot of personal information on affected users, including their full names and addresses, as well as their Google account activity. The feds also wanted all affected users’ historical locations. According to court records, while Google didn’t provide the information, the cops still found their suspect in the end.
Outside of concerns around government overreach, the FBI’s remarkable attempt to force Google to assist in its investigation will likely worry all who were disturbed by an Associated Press investigation published on Monday that claimed Google continued to track people even when they turned location features off. The court warrants unearthed by Forbes indicate some at the FBI believe they have a right to that location data too, even if it belongs to innocents who might be unwittingly caught up in invasive government surveillance. And the government feels such fishing expeditions are permissable; it issued the warrant on Google without knowing whether or not the suspect used an Android device or any of the company services at all….
What made the Maine data request unique was its complexity and breadth, asking Google to carry out significant work to find people who’d been in two locations, across multiple locations at specifc times, all in a single warrant.
We’ll return to Google’s actions later in this post.
A few months later, Forbes learned of another request for a reverse location search warrant, this time in Virginia:
The most recent order on Google, unearthed by Forbes earlier this week, came from the FBI in Henrico, Virginia. They went to Google after four separate robberies in which unidentified, armed individuals entered and stole from the same Dollar Tree store between March and September this year. The manager of the Dollar Tree was also robbed at gunpoint while dropping off money at a Wells Fargo night-deposit box located just down the road from the store.
The warrant asks for location histories held by Google for anyone within three separate areas—including regions around the Dollar Tree store and the Wells Fargo address—during the times and days the five robberies took place. The FBI also wanted identifying information of Google account holders in those areas, two of which had a 375-meter radius. The other had a 300-meter radius.
Google Maps shows that a significant number of residences, shops and restaurants are within the zones outlined in the warrant.
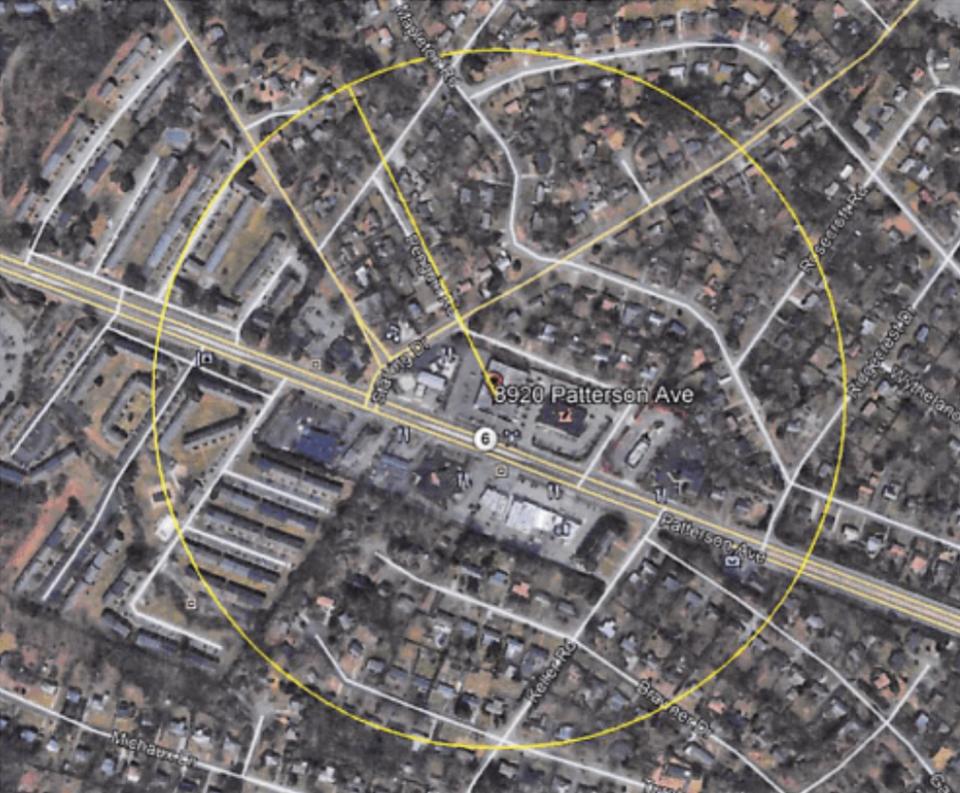
Now at least in the Virginia case, the images above were part of the warrant. But that isn’t a given.
The MPR article explains why the judge in that search (recall the first images in the post) signed off on a search warrant that covered such a large area and would clearly pick up a lot of innocent people:
On a map, it’s easy to visualize how expansive this warrant request was…
But the judge wasn’t given a map.
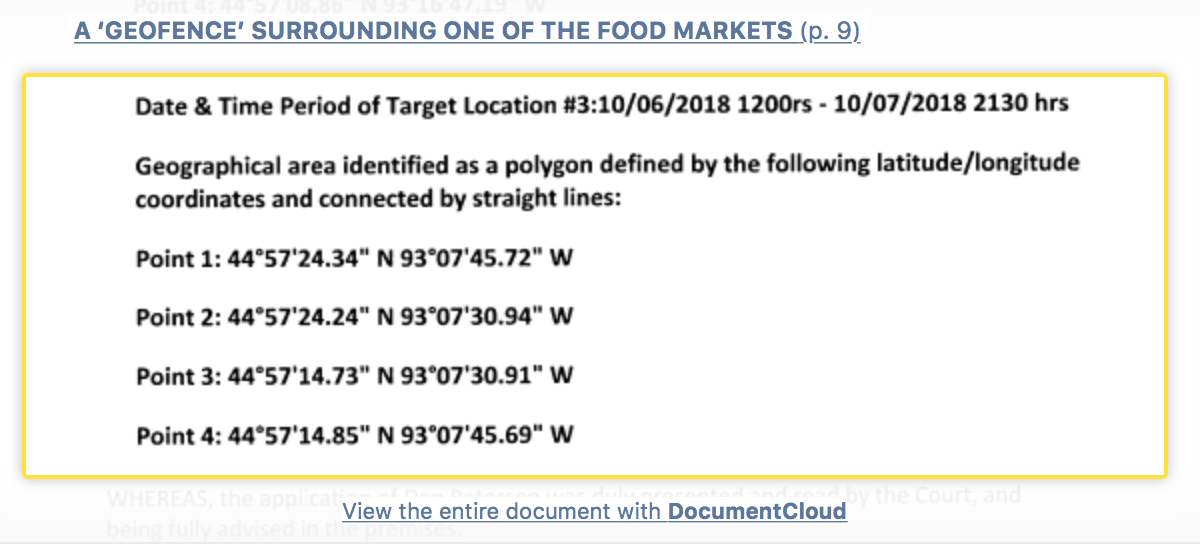
The warrant application did not spell out plainly the area covered by the warrant, what was inside the targeted areas, or how the areas were related to the crime at all. It used only technical language, specifying geographical coordinates of the target areas, also called “geofences.”
The judge approved the warrant application in about 10 minutes.
“Most human beings can’t interpret large strings of numbers and GPS coordinates without a map to illustrate them, and judges are no exception,” said Nathan Freed Wessler, an attorney for the national American Civil Liberties Union.
In at least one of the Minnesota warrants, the judge ordered Google to cough up more information:
There was a match, but not a great one. Police said it was near the gas station, but not the bar or hair salon, and the data point wasn’t very accurate.
“Google locations and their accuracies should not be used in a definite way,” read a study from a team of forensic data scientists last year. The research found that while Google’s data could usually place someone in the general whereabouts of an area, some conditions resulted in Google overestimating its accuracy 93 percent of the time.
In this case, Google told police the device was “within a 52 meter radius,” roughly 170 feet, of the gas station.
With that large a circle, a judge would have no way to know for sure if the device was the burglar, someone buying fuel, the business owner’s phone or tablet kept inside, or someone just driving down the road. Still, the device was spotted at 2:29 a.m. and 2:54 a.m., while the burglary was at 2:47 a.m.
It presented a tough probable cause analysis, and police were asking for a lot: the identity of the phone’s owner, billing information, phone numbers, and two months’ of their web browsing history and location data. Google was also put under a non-disclosure order, restricted from telling the user that this information would be divulged for at least six months.
No map was provided in the application to illustrate the area or accuracy level to the judge. This warrant was also issued within about 10 minutes of the detective requesting it.
Two months after Google turned over the data, no one has been arrested.
What Did Google Do?
As you can infer, from the latest cases, in Minnesota, Google cooperated. From the MPR article:
Brooklyn Park has also tapped Google for location data. While the company rejected some early versions of the police department’s warrants when they didn’t agree with the language, “they’ve been really good to work with,” said Mark Bruley, the city’s deputy police chief.
That wasn’t what happened in the Virginia or Maine cases. In both the warrants were issued by Federal judges, and Google just blew them off. It didn’t respond at all. In Maine, the court extended the warrant date four times, and was prepared to do so a fifth time, but the prosecutors gave up.
I find this part of the story as troubling as the warrants themselves. Google defies the court multiple times, with no consequences? At a minimum, a Google executive should have been required to show up to ‘spain himself. These incidents make clear that Google is a law unto itself.
Why These Search Warrants Are Unconstitutional
The experts are forcefully of the view that these reverse location search warrants aren’t kosher. Among other reasons, they fail to establish probable cause. The police can’t establish that the perp was carrying a device that was sending data to Google at the time of the crime.
In addition, the Fourth Amendment bars the sort of general search that these warrants represent. From the second Forbes article:
Jennifer Lynch, senior staff attorney at digital and human rights body the Electronic Frontier Foundation, said that the order in Hernico [Virginia] could’ve swept up the locations of thousands of innocent people. “Requests like this act as ‘general warrants’ and may violate the Fourth Amendment because they are not tied to a specific device,” Lynch added. The Fourth Amendment provides Americans with a right to protect themselves from unreasonable searches.
From WRAL, which covered four uses of reverse location search warrants in Raleigh, North Carolina, two for murders, one for sexual assault and one for suspected arson:
[Jonathan] Jones, the Elon professor and former Durham prosecutor, expressed similar concerns after reviewing the warrants. In particular, the fire and sexual battery cases didn’t present evidence that the arsonist or the attacker had a cell phone, he said.
“In those cases, the evidence provided to establish probable cause seems very thin to me,” Jones said. “These amount to fishing expeditions that could potentially snare anyone in the vicinity with a cell phone, whether they were involved in the crime or not.”
To Stephanie Lacambra, criminal defense staff attorney at the Electronic Frontier Foundation, all of the search warrants she reviewed are “deficient.”
“I don’t think with real scrutiny that they would hold up,” Lacambra said.
She also singled out the possible arson and sexual battery warrants, pointing out that the affidavits fail to link devices with the crimes.
“To just say, ‘Criminals commit crimes, and we know that most people have cell phones,’ that should not be enough to get the geo-location on anyone that happened to be in the vicinity of a particular incident during a particular time,” Lacambra said.
There is also a possibility that this approach will backfire. Recall that Google defied the search warrants in Maine, which included a request for a personal data dump on anyone who was “close” to two of the nine crime scenes. The police found their man, Travis Card, via physical evidence plus other cellphone data searches, and he pled guilty. From Forbes:
Card’s attorney said she had no idea about the government’s request for Google data until yesterday.
“I would have been all over it if Travis exercised his right to a trial. It is mind-blowing that the federal government believes this is not a blatant violation of privacy,” Heather Gonzales of law firm Strike Gonzales & Butler Bailey.
“Bottom line, when an investigation violates the Constitution, the evidence can’t be used at trial, which often results in dismissals of the charges, regardless of what the evidence was, which means some suspects who could have been convicted just walk right out of the courtroom. The hubris defeats the goal.”
And another wee problem, from the MPR News story:
Don Gemberling, an attorney who managed data practices issues at the Minnesota Department of Administration for more than 30 years, pointed to another consequence of these data sweeps: once the investigation is closed, all the data law enforcement collects become public information.
“That’s probably something that we’re going to have to navigate in the near future,” said Bruley. He said all the data are saved as part of case files.
Other Services Are in on This Game
while Google makes for one-stop shopping, it’s far from the only source police are using. From Forbes:
Captain John Sherwin of the Rochester Police Department in Minnesota said it wasn’t just Google that could furnish cops with a startling mount of detailed location data. Facebook and Snapchat were two others who’d proven useful, he said.
Sherwin told Forbes his homicide investigators recently served a court order on Snapchat to help it locate an alleged shooter pursuant to court order. Though not a reverse location search, the Rochester police used the Snapchat data and combined that with information from the person’s internet provider to determine the location of the alleged killer’s IP address, Sherwin said. Combined with “general intelligence” from friends and associates, police were able to locate the suspect.
And remember, if you look suspicious in one of these data dragnet exercises, the investigation is intrusive. From MPR News:
When Google provides location data in response to one of these warrants, police “put that location data into the software and then map out a ‘profile of life’ of where they go, where they travel, and where they were the night of the crime,” [Mark] Bruley [Brooklyn Park deputy police chief] said.
Most readers seem to have resigned themselves to being geolocated all the time. Maybe this story will encourage you to think twice about that.


I think this issue goes deeper than whether people let their google accounts track their location. Similar types of searches have been happening in the past, as in the case U.S. v. Graham – https://harvardlawreview.org/2017/02/united-states-v-graham/ has a short summary. I wrote a draft of an academic paper a few years ago (which admittedly didn’t make it very far towards getting published) that contemplated this issue but using as an example the automatic license plate readers that were installed all over US highways following 9/11 – that type of database also aggregates the movement history of thousands or millions of people and could be used to find the proverbial needle in the haystack like Google location was in these cases.
The example of airport security scanners distills many of the arguments with these searches. During the 1970s when there were multiple airplane highjackings, airports started installing metal detectors. To my mind, there’s no question that that is a type of search where there is something much lower than probable cause to scan and search every person. But most people who considered the problem were convinced that some type of search or scan was appropriate even in that situation because of the perceived necessity of addressing the plane highjackings – i.e. the importance of avoiding a catastrophic event was sufficient justification for a minimally invasive search of millions.
By extension, the practicalities of solving a string of robberies or locating a murder suspect, like preventing a plane highjacking, will probably convince law enforcement and a significant portion of the public that these dragnet searches with minimal suspicion as to any one person are desirable, or “reasonable” in 4th Amendment terms. To me at least, this explains why 4th Amendment law has turned into such a hodgepodge of “exceptions” and “non-searches” to the point where the law is a complete mess with minimal doctrinal coherence. Courts keep letting new invasive techniques flourish because they can find at least some use cases where they seem justified.
I think that the Swiss model – https://serval.unil.ch/resource/serval:BIB_6E5F1222109D.P001/REF.pdf (since repealed to some degree https://www.bbc.com/news/world-europe-37465853 ) points a way forward. The question is whether the invasiveness of any given search or search technique is proportional to the need to do the search. And for more invasive searches, more independent oversight and rules on data retention become more necessary. Basically, that would mean that the searches discussed in the article can only be done to investigate the most serious of crimes, would require extensive tailoring of the search (like limiting the geographic area of the dragnet and the time-frame over which data is gathered), would need independent oversight from a court beyond just approving or rejecting the search, and there would need to be a policy on what to do with the data, like deleting almost all of it, once the search had narrowed down a list of suspects.
In short, this type of tracking and surveillance will happen even if you give up your computer-phone – think facial recognition as an impending surveillance tool that will lead to the same questions – and we probably need a new legal doctrine to address it because the status quo is an inadequate mess.
> we probably need a new legal doctrine to address it
We have all of the law we need. B. of Rights amendment number four; NO unreasonable search or seizure. If the cops want it they need to specify what is it and get a judge to sign a warrant. It’s right there in the text of the Bill of Rights. What we need is to get rid of government officials who cannot be bothered to follow the law. Approximately 99.999% of the [expletives deleted].
Something similar has been used in Germany for many years. Although here the police does not use Google but the mobile carriers instead. They collect all call detail records originated in the cell(s) in which the crime occured, up to 10 weeks (!) in the past. I hope this helps people in other countries to prepare for or even better fight these policies.
More info (unfortunately only in German): https://de.wikipedia.org/wiki/Funkzellenabfrage
Recent statistics about usage of this instrument can be found here, only federal police forces are included: https://netzpolitik.org/2018/halbjahreswerte-fuer-stille-sms-imsi-catcher-und-funkzellenabfragen/
How is this different from gathering up video footage from all in the vicinity of a crime in hopes of spotting the perps either casing the joint ahead of time, or speeding away? Not that I don’t share your concerns, but darn it, they’re trying to apprehend the bad guys. What if it turns out they had the availability of this tool but didn’t use it, then said bad guy kills someone, or several someones? Maybe one of them is your Mom, or sister, then what? Feel the same? This ‘what if’ does make me feel different. No, I don’t like it, but putting it on the scale leads me to conclude better to give the cops the tool than protect me to the nth degree.
Personally, it still upsets me quite bit regarding cops confiscating money from people, where law enforcement subsequently keeps the money. Yikes!
—How is this different from gathering up video footage from all in the vicinity of a crime—
bingo. it’s all about which judicial lens/analogy one uses. Is your cell phone (when it’s pinging a tower) more like you walking in front of a CCTV camera?
Is your cell phone (when it’s not pinging a tower and retaining it’s location history) more like your personal diary?
The difference between using video evidence from a crime scene and tapping into the phones of up to thousands of people in the crime scenes general area is that the latter effects more people and is far more invasive. I don’t want police to physically search me and my home just because I was near a crimes scene, similarly, I don’t want police combing through my digital footprints.
Recently, a women where I was working gushed over an impending vacation to Jamaica. She then opined that she was concerned with the street crime. She was comforted by others that she would not be exposed to it as she would be staying within a resort.
I struck up my own two cents when I noted that the womens’ bank was probably accountable for crimes several magnitudes greater than street crime and was greeted by looks as if I had two heads.
Video doesn’t have any of your personal data.
John, might I offer that that sounds like the argument that gets people behind the thinking of Jack Bauer: got to lie, spy, kill and torture on the off chance that the Law might keep The Terrorists from detonating a nuke/releasing a plague among us. Abu ghraib and Guantanamo are a couple of endpoints, along with other gulags and interventions.
Anyone follow police clearance and conviction statistics? These are of course gamed, and I hear that in Dear Old Blighty the gaming is far worse than here. Even with the benefit of gaming, the rates of ‘effective enforcement” are, shall we say, low. Police are mostly RESPONSE entities, when it comes to crime other than “crimes against the state” like Occupy. When they respond at all. Some of them may be “trying to apprehend the bad guys,” but that is hardly the substance of what they mostly do. Good luck with apprehension of the mope that burgles you, or recovery of your stuff.
And in lots of places, like Chicago when I lived there and maybe today, there’s this concept among the law enforcement “community” of “misdemeanor murders,” not worth investigating or seriously prosecuting (plea bargains and corruption and other social defects, like labeling so many of the current shootings as just “ghetto crime.”) The job opening that landed me a decent lawyer gig with the US Environmental Protection Agency happened when the man I replaced was found tied to the posts of his bed with his throat slashed. Joe was gay and apparently took the wrong person home. There was a pattern of similar murders at the time, but no one ever was arrested, and no police came to inquire from the folks who knew him about his habits and contacts and movements.
“Predictive policing” is state terror, however dressed up in Big Data AI clothes, including all this “data harvesting” from among us mopes’ nearly necessary electronic devices (lots of very smart people feeding the addictive responses of the rest of us, whether opioids or “smart phones” and these multi-player games that displace meatspace community.
Looks to me like all of this is now completely baked into the “system” and inevitable. But to believe or hope that the Law will use all this data, all these images, for “public benefit?” That really stretches the definitions and ignores the reality of how “our” political economies have actually manifested and evolved.
You and I have no “rights” that we cannot effectively enforce. What “rights” do I think we have? Pretty much limited to the “right” to try to stay small and inoffensive and impoverished enough to not be worth the attention of the system.
Ahem, the US is not central London and we don’t have CCTV cameras deployed by the city even in Manhattan. The cameras are private cameras, overwhelmingly focused on doorways and in lobbies. They don’t track you on the street the way CCTV cameras in Central London do.
Nice try, attempting to depict being photographed when in convenience stores as being anything like being constantly geolocated by your phone.
You have to admit that a Reverse Location Search Warrant can be a great tool for police. As an example. Suppose that there is an anti-fracking meeting in a large building downtown. Well, the police could drive by that building and then demand from a friendly Google what mobiles were in the area as well as the phone’s owner, billing information, phone numbers, and two months’ of their web browsing history and location data. The police then get basically a roll-call for everybody at that meeting plus all the other info that can then be sent on to one of those fusion centers The same can be done for a street protest by having a plain clothes cop walk through the middle of that crowd. Just imagine if Nixon and the FBI had that capability back in the 60s to use against the anti-war protesters.
So right it makes my teeth hurt, RevKev. Cell phones are convenient for everyone, esp the so-called Law.
Or, if some people working for Trump talked to Russians, that info could be scooped up and given to FBI and Mueller. That will be “leaked” to the Corporate Media and they will know what to do with it.
Of course, they would not need to watch Hillary or anyone but Trump because it’s ok for anyone to talk to Russians as long as they don’t suggest we should end a few of our Forever Wars or some other Holy Grail of Establishmentism.
does it help to have the phone off? battery removed? But people would have to do that BEFORE they went to the meeting.
And what makes us think they aren’t already doing this, using tower spoofers and skipping the warrant?
I am acquainted with several practical paranoids who carry there phones in Faraday bags or containers, only taking them out for use. Just a thought.
Terence
Obviously, we should make cellphone ownership mandatory. For people’s personal safety.
I think you mean “Raleigh, North Carolina,” in the paragraph above the “from WRAL” excerpt.
Fixed, thanks!
I don’t have a phone, smart or dumb, as I have a problem with voluntary permanent surveillance devices. I have (carried) a tablet, several actually, and have regularly checked the data that Google has collected which has shown me at the same location, home such as it is, since Google has been tracking such data. [Extremely early alpha/beta tester from their beginning.] Now it looks like I need a burner tablet, just in case, to read my electronic books, methinks. Not fun to create but it can be done. That, or have paper books to read now and again.
Deus ex machina.
Just turn off any radio capabilities and keep it in a Faraday bag.
“Turning it off” does not necessarily turn it off. This is well known in the IT/communications/security communities They can also be remotely enabled and locally. invisibly enabled by malware on the device, similarly well known.That’s also the case with location via cell tower’s signal strengths, GPS, microphone and camera. A “Faraday bag,” as you refer to it but normally known as a “Faraday cage,” still allows the system using its sensors and recording such whenever out of the bag and still doesn’t prevent motion sensing for use in dead reckoning. And such can be fed back to Google et alia at a later time, also a known thing. The literature is very extensive around all of this and I’ve spent a long time immersed in these communities due to my heavy engineering background, military security background, and interest in all things political-economy. Plus, the government is at the center of my threat-model. Current/future activities are the hazard. Everything else is well known either due to my security clearance, veterans health-care or via the various hacks (OPM, VA, &c.) in the case of foreign actors. Even the information brokers get to play with my hideously large dataset. The data that is “out there” is something I keep as close a note of as I can. I call this personal due diligence.
I don’t need such devices: Send me an email, I might get back to you. The risk/ROI isn’t even remotely balanced in my case. Even the government knows to send emails! I do understand why people find these devices useful. I’m not one of them.
Thanks for the details. The Faraday Bag remark references the multitude of soft Faraday Cages available at retail.
Briny, thank you for your reply, I was reading these comments specifically to find information on the “Faraday bags” (the products are marketed with these names; actually, they look more like wallets).
Is there a single book or website you recommend to get a good overview of these issues?
Also, I would have thought the Faraday bag would be the best option. Unless, of course, using such a device is used as evidence against you, just like deleting your browsing history can be (falsely) claimed as a criminal “destruction of evidence.”
Here is a limitation of Faraday bags I wouldn’t have considered:
Two, although eff.org is already known to this community. The other is where I found links to this site from some kind soul so likely not out of place to post here: schneier.com. His books should be considered required reading by anyone with some level of concern around these topics. “Data and Goliath” and “Click Here to Kill Everyone” are dead on topic and immediately relevant.
The comment threads can get more than a little deep but the posts themselves are quite accessible. Fridays there’s an open comment thread. Don’t hesitate to ask questions, we don’t bite.
The problem just isn’t with phones. Sure, it’s easy to say just don’t use a cell phone. But this technology is already built into cars and other devices. 5G is coming and it’ll be built into almost everything.
What about RFID chips? Or the next gen of them? Facial recognition?
Google checks your location up to 14000x day. They probably know how long you spend in the bathroom.
The technologies are coming (and here) that will allow people (governments) to track our every move. We need to decide as a society how that will work. And, we need to do it fast.
It took me less than 15 seconds to conceptualize turning ATM/credit cards into surveillance devices including then issues involved in powering them from the ambient environment, sensor arrays, transducers, storage, etc. and I’ve the tools (engineering, simulation…) to execute it. But there’s no way I’m putting such a design anywhere outside a secure environment (and my ideas on what’s secure are pretty extreme).
Now, the reality is that there will never likely be any restrictions on the use of such technologies as they serve the interest of our “masters” despite what any small segment of the rest of the populace may demand. I don’t see that changing. Thankfully, I’ll not be around much longer (terminal illness) and have no hostages to fortune. I do wonder if all species end up destroying themselves this way.
[I’ve been inventing things my whole life and stop to think long and hard on how such technology will be misused. Rather a lot will never see the light of day.]
> Google checks your location up to 14000x day.
That is a bit over once every six seconds. A colossal, parasitic drain of electrical power from both ends, when everybody charges their phones, and Google running servers in locations where they get cut rate power prices not available to anyone else. Lots of consumed energy so Google can sell an ad to someone trying to get you to buy their crapola, and that’s the benign take.
Same thing with Spamazon. A couple of weeks ago in links were articles about a woman trying to get by without any contact from Amazon, and the damn apps called home 300,000 times in a week.
Which is worse for the environment? This tech bro spying idiocy on the masses or Elon Musk flying in a jet spewing CO2 everywhere.
Stop the spying and save the planet.
> A colossal, parasitic drain of electrical power from both ends, when everybody charges their phones, and Google running servers in locations where they get cut rate power prices not available to anyone else
Has anybody done the math on this power consumption and greenhouse gasses?
If I turn off the GPS locator am I safe?
From what I hear, no. Maybe consider a Faraday bag but you won’t be able to get incoming calls & messages until you take it out of it. Or, alternatively, just leave your mobile at home.
Or, alternatively, just leave your mobile at home.
And your face.
In fact, probably should not live within a mile of anyone else and never leave your Faraday home. Does Sunday morning television sell Faraday windows and siding yet?
Don’t shoot the messenger, mate. To me a mobile is just a tool and not part of my identity. If I am going downtown then I usually don’t bother to take it. If I am going on a long trip then I usually do. Hmmpphh, us Luddites don’t get no respect!
I carry a tracfone and that does for emergencies.
Cost: $20/every 3 months and I think it cost me $25 originally (have had it for at least 6 years).
Have a tablet at home.
Cell phone triangulation way less precise in location than GPS, plus your provider keeps data only when you are using it (ie, you are not tracked between calls unless someone gets a warrant to locate you going forward). There are court precedents that have also found that triangulation is too approximate to locate a phone user at the scene of a crime.
Not shooting at all. Just bouncing along…) I live in a remote valley somewhat near the insulation of Faraday naturally. People are appalled when I tell them if they want to text they have to go outside, about a hundred steps in front of the house for a sweet spot.
I do leave my mobile at home. It’s not hard. And please tell me where you face is actually recorded when you are out and about? Even here in Manhattan, private cameras on buildings are aimed at doorways and don’t pick up foot traffic much/at all depending on their orientation. And they aren’t very good. When I lost my laptop in a cab, even though I had a very precise time of arrival (w/in 15 minutes) my building looked +/- 2 hours on the tape and was unable to find me entering the building.
I wish I felt confident about Faraday bags. You can test if they receive cell phone calls but they use other frequencies too and you can’t readily verify whether the bag is blocking them too. Any reader suggestions here? One of these days, the network upgrades are going to force us all off dumbphones.
Removing the battery is about the best you can do and that’s not possible on very many phones today. “I wonder why?” Aside from planned obsolescence that’s just my deep paranoia talking.
During the Iraq occupation, the resistance learned to remove the SIM card from their mobiles when not in use.
That’s what I thought re: the batteries, but making batteries hard to replace also functions as a kind of built in obsolescence, which I think is the more likely cynical explanation.
Ms Smith
Depending on you business or corporate trust issues, faraday bags . com claims to block all signals with their products. they claim independent testing. Any gear heads with “experience”, radio waves used are generally will very ( they have expanded the spectrum as more frequencies are needed. As cell phone jammers are illegal except for government use ( prisons are most common I recollect ), consider a low power jammer in the Faraday bag with your phone, yes another battery, and no I have not researched how practical or not this idea is.
Terence
If you read the AP story that kicked off the controversy about Google and location they say that you can completely disable tracking by turning off ‘location services”–a fairly straightforward setting in your Android settings–and also signing into your Google account and turning off “Web & App Activity.” Here’s how for the latter
https://www.wikihow.com/Turn-Off-Google-Web-&-App-Activity
It’s also possible to use an Android phone without any Google account at all but you will have to “sideload” apps obtained off the web or by using a different Android device. I know that this works because I do it myself.
Of course if you assume that Google or the NSA are always tracking you regardless of the phone and account settings then any steps an individual takes short of not using a phone won’t help. But I don’t think that’s the kind of surveillance the MPR story is talking about.
> If I turn off the GPS locator am I safe?
How would you know it’s really turned off?
Two questions for the readership, and thanks in advance for the help and/or advice :
I use an ancient Samsung dumb phone. My understanding (please correct me if I’m wrong) is that law enforcement could only trace my general movements by issuing a subpoena, specifically for that device, to the phone company. Is that so?
However, I recently purchased a I-Pod Touch, in order to back up my music library (usually accessed on a now-discontinued model with no Internet access). This device does everything a smart phone does, except make phone calls.
The question is, even though I’ve turned the Location Services off, and keep the I-Pod turned off when carrying it as a back-up when traveling, I assume it can still be tracked in real time. Is that so?
If it is, time to get a Faraday Cage…
Please read the article above carefully. It answers most of your questions.
Re the iPod, if it si more recent than I believe a third gen, it GPS locates you. If you install Google Maps, Google has access to your location data.
Over time this may become a weakness. The more they think that everyone has a smartphone, the better. Those of us who don’t, who don’t even carry their dumb phone very often, and avoid the platforms, are going to become more invisible. Not entirely (cameras, etc.)
It’s easy for people to become overly reliant on technology and this also causes the loss of certain skills. Good example is simpler arithmetic with the advent of calculators
another consequence of these data sweeps: once the investigation is closed, all the data law enforcement collects become public information.
This was something I was thinking of, google has tons of info that it can’t exploit unless it can somehow “out it”. This scheme would seem to work to that end
when you compare how closely we monitor people compared with how loosely we monitor guns, it is clear that public safety is not our concern
https://www.gq.com/story/inside-federal-bureau-of-way-too-many-guns
There’s no reason that one has to leave their phone turned on, or not wrapped in a RF shield, except at certain times of day. Some phones, even when turned “off” have a battery backup that may track your location. The aluminum foil wallet or more elegant solutions prevents that.
I only receive calls on the hour and half hour by prior arrangement with friends. It’s refreshing to not have to constantly answer the thing, plus I’m not frying my testicles or eyeballs or brain by having it constantly pinging its location to the nearest cell tower around the clock.
I have a lawyer question. So a crime is committed and the popo get their reverse location warrant. What happens if they are not able to find the perpetrator of the crime they got the warrant for, but after searching a few hundred phones they discover other crimes unrelated to the warrant?
It seems to me that any evidence found this way would be inadmissible in court as well as any evidence found subsequently that was based on the knowledge from the searched phones.
So this policy could have the effect of letting criminals get away, although the way things are going, my guess is that if this started to actually happen our Congresspeople in thrall to the surveillance industry would simply pass a law saying these types of searches are no longer in violation of the 4th amendment.
Should smart phone users be concerned about unauthorized remote access to their cameras and microphones, in addition to the geolocation items noted?
With a computer, one may cover the camera and use a dongle or similar to try to disable the microphone. Those prophylactics may not work with phones, even with the features switched off in settings.
What we need is some form of modern satyagraha….
Keep changing phones at a massive scale… that the authorities give up in frustration :-)
What we need is a modern satyagraha :-)
Keep changing phones at a massive scale & rate that authorities are confused and give up the whole concept in frustration…
Most of our data is in the cloud anyways…
a la Thomas Crown Affair
Briny thanks for your technical insights
From what I can gather, there are a few issues only defeated by the decision to ‘leave phone at home’
One is that a phone switched off is not an assurance – more so for apple products, known to have additional power sources built in.
Another is ‘store and forward’. This means, data stored waiting for the chance to power up/make an internet connection. Can a phone have a hidden power source, and a spectrometer able to monitor how far the phone has travelled since the last known GPS ping, and store that data ready for the power to adequately process it/upload it? There are probably all kinds of built in capabilities not made known to the public, not even in Snowden documents
It is possible for a tiny chip to hold a 3G connection and internal power source, independent of everything else the phone is doing, and not even detectable to visual inspection. Defeating all air gaps. This has been discussed on schneier.com
Spectrometer would be for a different purpose. Simply using the built-in motion sensors (which can also be used for gait analysis as a fact in passing) with intermittent GPS fixes is fairly accurate, more so as you can use the GPS fixes to tune the dead reckoning. I actually know that hardware/software combination from back in the day in the military. And, yes, Bruce Schneiers schneier.com is a wonderful resource. I don’t participate much in the comments due government enforced NDA from the nether regions. When the NSA types couldn’t fix their gear, well guess who they got? Thankfully there are wide areas where I’m stilled allowed to play. AI/ML dates back to my preteen years, well before they got their hands on me.
Yves – An interesting typo: “Google deifies the court multiple times, with no consequences?
Not exactly…
Haha, fixed, thanks!