The Sacramento Bee and the author of its State Worker column, Wes Venteicher, are a sad case study in what is happening to soi-distant journalists in the US.
Once upon a time, the Bee’s most widely read column, the State Worker, showed considerable independence. When Jon Ortiz penned that feature, he would regularly call out questionable conduct at CalPERS.
But under his successors Adam Ashton and the current columnist Wes Venteicher, the State Worker feature has devolved into propaganda for CalPERS. Later this week, we’ll discuss how Venteicher blew the story on CalPERS divestment from private prisons, a move has significant implications lost on Venteicher due to his apparent lack of inquisitiveness.
But on to more pressing matters, which is the latest example of how CalPERS at the Sacramento Bee are conniving to embarrass themselves and in passing, throwing CalPERS vendor Diligent Boards under the bus.
Venteicher is working on what looks like the oxymoron of a pathetic hit piece on CalPERS’ pro-transparency board member Margaret Brown. It’s pathetic because Venteicher’s line of inquiry shows he’s got nuthin, yet he’s acted as if he really believes Something Serious is afoot.
To cut to the chase, the line of attack is that CalPERS issued electronic devices like cell phones and tablets to board members and newly-created CalPERS documents show that Brown lost some of them. In reality, Brown has already returned all those devices save one iPad to CalPERS, and as we’ll show shortly, Brown still has the iPad and it was never at risk of being picked up by anyone else. She mistakenly reported it as missing when it had fallen behind a large cabinet in her house while being charged.
On top of that, lost devices are a fact of life. Both CalPERS and its board portal service, Diligent Boards, each have security protections to prevent access to data. Yet this non-event is being trumped up as some sort of security risk.
This sort of thing wouldn’t make the crime blotter in a 500 person town. The fact that Venteicher is devoting what ought to be valuable reportorial time on a nothingburger illustrates how over-willing he is to carry CalPERS’ water. This sort of piece would get him laughed at in a city like New York where reporters are capable of finding and reporting on bona fide news. If Venteicher wants to guarantee that he never gets out of provincial backwaters like Sacramento, this is just the way to do it.
If the story hews to Venteicher’s line of inquiry, it’s based on two false premises: first, that Brown lost (as opposed to temporarily misplaced) devices and second, that had they actually been lost, that CalPERS and Diligent Boards’ security procedures we so lax that CalPERS’ secrets could conceivably have gotten out in the wild.
As we’ll show, this story was almost certainly fed to Venteicher by CalPERS. His wrongheaded insinuations follow the CalPERS pattern of smearing dissident board members while failing to publicize large lapses in the very same vein by the staff-captured board members and senior executives.
Mind you, not only were all Brown’s devices “found” but it’s arguably a matter of nomenclature whether to have deemed them to have been lost. For instance, record of the status of the iPad that Brown is listed as not having returned is inaccurate. Brown found the location of her iPad after she returned home from Sacramento and informed a CalPERS staffer. Yet CalPERS created documents that it gave to Venteicher that showed the reverse. Was this incompetence on CalPERS part, or a deliberate effort to mislead?
Brown sent this image to show she has the supposedly missing iPad that is the focus of this tempest in a teapot in her possession:

On top of that, in the topsy-turvy World According to CalPERS, Brown is guilty of being scrupulous. As she said,
As someone who has managed large projects with budgets of hundreds of millions of dollars, I’ve always been relentless in accounting for funds and assets so I could hold the people around me to the same standard. If I can’t put my hands on a credit card, even though I am very sure that it’s in the pocket of a jacket I left in my locked car, I’ll cancel it rather than run the risk that I might be wrong.
The fact that CalPERS also unwittingly makes clear its records are shot full of holes separately tells you how seriously CalPERS takes asset-tracking.
Genesis of the Probable Brown Hit Piece
The Sacramento Bee sent a Public Records Act request to CalPERS asking for
…records of all electronic devices, including phones, tablets and any other devices, provided to CalPERS board members in the last five years.
If you believe someone at the Bee all on his little own dreamed up that of all the possible things they could ask CalPERS about, the topic the status of CalPERS tech toys merited a Public Records Act request, I have a bridge I’d like to sell you.
Further evidence of the lack of independence of this PRA that CalPERS created documents just for the Bee, not just once but twice.
The spreadsheet that CalPERS initially sent to the Bee was created on September 30, 2019 by Larry Hughes and modified on October 4. Public Records Act requests require the production, not the creation, of documents. CalPERS did not provide the Bee with any records as required by the Public Records Act.
Yet CEO Marcie Frost represented to the board that this was the sum total of the records provided to the Bee. On October 9, she sent a copy of the spreadsheet and only the spreadsheet to the board, stating: “Attached for your information are the records provided to the Bee.”
The first spreadsheet was obviously incomplete, since it has no information about devices issued to former board members Ron Lind, Richard Gillihan, JJ Jelincic, Michael Bilbrey, and George Diehr and current board members Jason Perez, Lisa Middleton and Eriana Ortega.
Someone on the receiving end must have been alert enough to notice and point the gaps out to CalPERS. The very next day, Frost sent out a second version of the spreadsheet with more board members added to the end of document, noting” “Attached is the remainder of the responsive records to the Sacramento Bee’s Public Records Act request.” The second spreadsheet looks to be an edited version of the original, since it was created September 30, 2019 by Larry Hughes and last modified on October 10, the same date as Frost’s second e-mail to the board.
We have embedded the later version as best we can at the end of this post; we can only provide a PDF. We will e-mail both spreadsheets to anyone who requests them. Bear in mind that the second version is still incomplete; it has no information about former board member George Diehr or current member Eriana Ortega. Both versions also have no information whatsoever about the “designees” of the Treasurer, Controller, and the Director of CalHR, who also have CalPERS-issued iPads. For instance, there is no information about current designees, who are regularly identified in CalPERS transcripts as “Acting Board Member,” such as State Treasurer Fiona Ma’s designees, Frank Rufino and Matt Sahaor and Betty Yee’s designees, Karen Green Ross and Lynn Paquin or earlier designees, such Grant Boyken, who was one of former Treasurer John Chiang’s designees.
With so many gaps, this spreadsheet on its face can’t be seen as saying much, save confirming that CalPERS does a poor job of asset-tracking or that CalPERS couldn’t be bothered to comply with this PRA even for a pet reporter.
The spreadsheet shows, among other things, that CalPERS assigns board members Apple devices, including the iPhone 6, 6s, and 7, as well as iPad Air and iPad Air. Board members have also sometimes cracked their screens or had bad batteries. Quelle surprise!
It also shows board members that lost an iPad: Margaret Brown, Priya Mathur, Ramon Rubalcava, and Theresa Taylor. Note that Brown has lost the most devices but is the only board member to have told CalPERS they were found them later, consistent with her claim of vigilance.1 By contrast, the spreadsheet shows Theresa Taylor also lost an iPhone 7 and didn’t notice or didn’t bother reporting it; she has one listed as found but never reported as lost. Or are these records inaccurate as well as incomplete?
Now, I applaud all of you for having read so far, since this all seems like a heap of nothing, correct? We finally get to the fun part, the e-mail from Venteicher to Brown yesterday, October 21, at 5:43 PM PDT:
Ms. Brown,
I’m the state worker reporter at the Sac Bee. I filed a Public Records Act request with CalPERS on all electronic devices distributed to board members over the last five years, and in the data saw that you have lost an iPad and two phones, and that the phones were recovered. Has the iPad been recovered?My understanding is iPads, at least, may be used to access both closed session and open session board materials. The closed session access would seem to make the loss of one of these iPads a security risk for the organization. Please give me a call at 916-321-1410 tomorrow to discuss this. I’m looking to talk by 5pm (Tuesday) for a story. Thanks.
—
Wes Venteicher
The Sacramento Bee
wventeicher@sacbee.com
(916) 321-1410
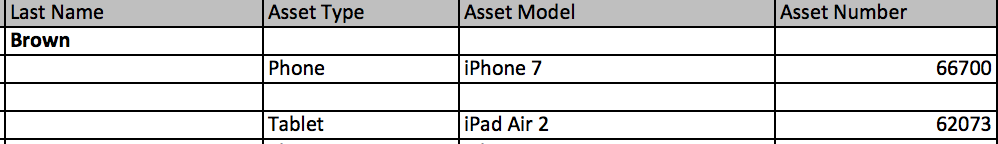
We’ve collapsed some of the columns that weren’t germane to show you Brown’s device rap sheet:
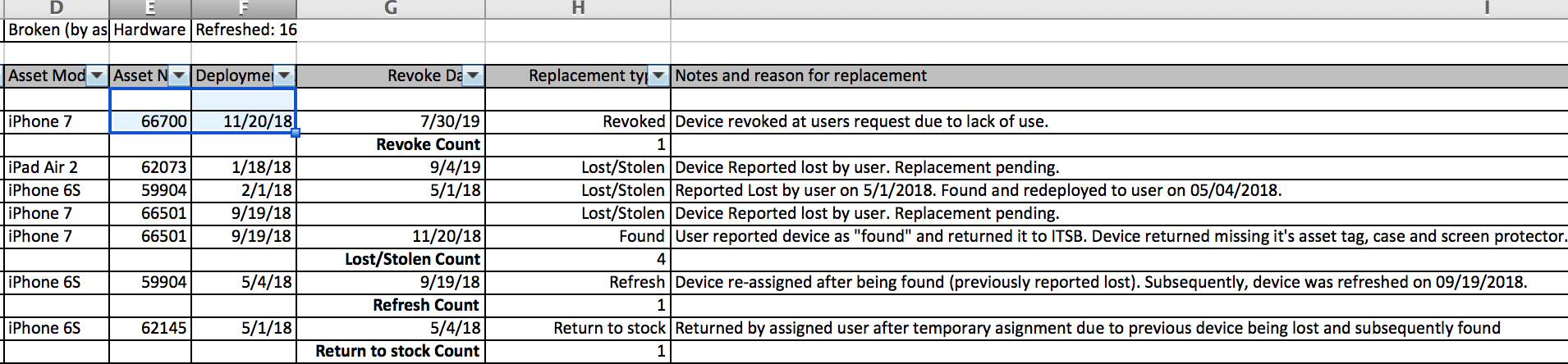
And here are the cells that show the asset tag for her iPad, so you can see that the number in the photo above is the same as the one CalPERS assigned to her, 62073:
 :
:
One has to wonder if Venteicher is also making inquiries of the board members who lost iPads and never recovered them. One also wonders if Venteicher knows that Diligent Boards can be accessed by desktop, laptop or smart phone.
Venteicher’s Ludicrous Security Insinuations
In what looks like an attempt to indict Brown, Venteicher takes an unwitting and large pot shot at CalPERS’ security practices as well as those of the vendor CalPERS uses to operate its “board portal,” Diligent Boards. In layperson terms, that means Diligent Boards hosts CalPERS closed session documents and public board meeting documents for board member access. For Venteicher’s concerns to be valid, both CalPERS and Diligent Boards would have to be grossly remiss.
As an aside, it’s par for the course that Venteicher treats being able to access open session records as a concern. Is he so clueless that he does not realize that anyone with an Internet connection and a search engine can find them on CalPERS’ site and/or YouTube?
JJ Jelincic reports that when he was on the board, CalPERS would perform a factory reset on iPhones and iPads reported as lost. That would make it impossible for anyone to ascertain anything if the device had been reported promptly as missing. Has CalPERS downgraded its security by abandoning this pratice?
As far as the iPads are concerned, Venteicher should know or have bothered to find out that they have an Auto-Lock feature which locks the device after a period of disuse, requiring a password or finger scan to re-open. The default time is short. If CalPERS were competent, it would issue devices with a quick trigger on the Auto-Lock and if possible, prevent users from changing that setting.
Perhaps Venteicher has also forgotten that Apple devices are famously hard to crack.
Perhaps by later today, Venteicher would also have worked out that in order to access closed session records, someone who had gotten their hands on a board iPad would not only have to provide a username and password for the device, but also a second username and password to access the Diligent Boards portal where copies of CalPERS’ closed session records sit.
Although I am in no position to evaluate Diligent Boards’ claims, its 3500 clients clearly regard security as of paramount importance. Accordingly, it is top of the list of considerations for potential customers:
Security is the #1 worry of boards adopting a new technology, and with good reason. Hackers work 24/7 trying to break electronic security and gain access to an organization’s systems to spy, steal, or extort. Often, hackers are able to do this without a company even knowing its security has been compromised. If you want a secure solution, you need state-of-the-art security methodologies and encryption – not just another file management system for your board. Portal software allows a business to feel secure in knowing their confidential and financial information is safe – or at least it should. Make sure any potential vendor makes you comfortable with their security practices for your data. However, remember that even the most secure route must also be the most user-friendly or board members may try to find a (less-secure) workaround.
An MIT computer science graduate and trustee tells me that companies like Diligent Boards typically offer more than one level of security protection. For instance, they might allow customers to choose between a simple user ID and password versus two-factor identification. So if CalPERS were concerned about security, it could probably opt for more stringent safeguards. Diligent Boards did not respond to questions.
Could the Planned Story Have a Different Primary Angle?
It is entirely possible that the Venteicher’s apparent intent to depict Brown as a threat to CalPERS’ vaunted security is merely a thread in a larger piece. After all, from CalPERS’ standpoint, if it gets a smear into print, it’s a gift that keeps giving. They can keep repeating it no matter how false or trivial it is in reality.
CalPERS is pursuing the half-baked idea of bringing the board software system in house, allegedly because the not-too-bright-bulbs in the Board Services Unit have taken to using Diligent Boards as a scapegoat for being late in uploading documents for the board to see before board meetings. Note that staff had no such problem with timeliness under former CEO Ann Stausboll.
If 3500 companies, most of which have more employees, more complex operations, and hence more ground for the board to cover, can navigate Diligent Boards, the problem seems to be staff not doing the work to become familiar and/or not seeking help.
In addition, if it really is true that Diligent Boards has become more cumbersome, there are competing services such as BoardAdvantage and Director Point. There is no evidence that CalPERS has assessed alternatives rather than embarking on a costly exercise in reinventing the wheel.
On top of that, CalPERS is hardly in a position to make a stink about security threats, let alone flatter itself it can build and run a sufficiently secure system given its IT lapses, such as:
1. A CalPERS employee hacking into CalPERS’ personnel records and altering them, then presenting the falsified documents to members of the state legislature (the Nancy Michaels case).
2. CalPERS issuing sequential passwords in a shared format to board members and senior executives, making it easy for anyone who knew the protocol to access the system.2
3. CalPERS failing to protect beneficiary records by letting a company with which it had no contract have access to its member database
4. A CalPERS employee left comments on our site that revealed mid-level network deficiencies
In other words, there are no good reasons for CalPERS to create its own, sure to be costly-to-build in house board portal. That suggests there are only bad ones. The most likely is that staff will spy on whether particular board members have looked at particular documents. Commercial board portals deliberately do not have that capability to protect board members from staff snooping and even more important, to protect individuals and the institution from liability (the failure to look at documents could be used in court to prove negligence).
Even though this is a sorry little tale, as Lambert said, it shows CalPERS is fractal. No matter what aspect you look at, the same patterns appear over and over: the reflexive dishonesty, the incompetence, the belief that all that matters is PR, the vicious attacks on those who are trying to get CalPERS to shape up. CalPERS is like an addict that needs to hit bottom and look at his dissolute life and the damage he’s done to others in order to have a hope of getting on the road to recovery. But with all those billions to burn, it’s going to be a costly ride.
____
1 Brown indicates, and I was not able to independently able to verify as of publication time, that the reason for the sometimes lengthy gap between when a device was reported as lost versus found is that CalPERS appears to have been inconsistent in logging her devices as found. Sometimes it appears to be based on her verbal report as to having them in her hand; other times, it seems not to have been logged as found until sighted by or returned to CalPERS.
2 This glaring deficiency makes Venteicher’s line of questioning less outlandish….if you assume the person who got their hands on the board device was a CalPERS staffer in the know.
00 CalPERS Second BOA Mobile Device list - With Names

In what looks like and attempt to indict Brown, Venteicher takes an unwitting and large pot shot at CalPERS security practices as well as those of the Vendor CalPERS uses to operate its “board portal”, Diligent Boards.
Venteicher: Ready, aim, backfire!
https://www.youtube.com/watch?v=hz65AOjabtM
beep beep.
(This latest ineptitude from CalPERS would be funny if its ineptness wasn’t so serious a problem for CalPERS retirees.)
Good point about CalPERS being fractal.
Thanks for your continued reporting on CalPERS, PE, and pensions.
Just got time for a brief comment here. I see that Wes Venteicher is new to the SacBee after joining at the beginning of the year. The article welcoming him said “He has a lot to learn about the state’s government and its workforce” but from what I can see, he will make a good fit with Adam Ashton and the SacBee so “Welcome to the party, pal!”
I would contend that the accuracy of that spreadsheet is irrelevant as it is only a wrapper for the one entry that is really of interest – that for Margaret Brown. It did not need to be accurate or complete. It could have had Brown’s entry all by itself. So, lets get a definition or two set here-
“hatchet job”
noun: informal
noun: hatchet job; plural noun: hatchet jobs
a fierce written attack on someone or their work.
“He does hatchet jobs, not reviews”
I was trying to look up the definition of the word “hack” too but mostly these days it has a definition to do with computers and not its earlier meaning. I am wondering if this attack is the thin edge of the wedge to try to stampede CalPERS into abandoning Diligent Boards and justifying it with non-stories such as this. If they want to bring security in-house, it would be glorious. I can see it now. The vital username would be something like admin and the password would probably be guest.
I did note one oddity. In Margaret Brown’s “rap sheet” it was charged that when Brown found and returned her device that it was missing its “asset tag” but that image clearly shows it to be still in place. But when you get down to the gist of this story, I think that we all know who the real CalPERS asset is here.
Etymology 3 in Wiktionary shows the source as:
a horse for hire especially an old and tired one (16th century). Subsequently, “a person, usually a journalist, hired to do routine work” (17th century).
It’s like a master class in skullduggery, except that the perpetrators are not so masterful. They do appear to be very persistent, however. At a convenient time in the future, this article can also be trotted out as independent confirmation (see, we’re not the only ones who think this) that board member Brown, although her heart is in the right place, just isn’t up to performing her duties. Please vote for candidate X. It seems the shenanigans will not end until they are successful in eliminating any meaningful board oversight, or they are ousted and jailed.
As someone closely involved with all aspects of IT Security within a specific subset ( a much smaller subset than CalPERS, I’m sure) of the DoD, the first thing that struck me is how lax their security practices are. An on-going, up-to-date, and accurate, inventory of IT assets is a fundamental key piece of basic security.
This is not equivalent to “Quick, put together a list!”
Based on this article it’s pretty clear that CalPERS is seriously deficient. Anyone with a basic understanding of IT Security, especially within a large financial institution such as CalPERS, will clearly see the SacBee article as veiled hit job on Margaret Brown, as well as a clear admission of ignorance of IT Security practices.
Mr. Venteicher also appears to show obvious ignorance in this field and so should not be writing anything about it until he is a little bit better educated.
I love the “CALPERS ASSET” sticker on Brown’s iPad. If only they were as careful with all their assets.
That tag might as well read “Steal Me”.
A proper asset tag would be meaningless to a casual observer.
I’m amazed, AMAZED.. not
What I am amazed about is that someone in Cal manages to write an article on corporate security w/o seemingly talking to any of the people who actually do corporate security. Because if he did, he’d know that dealing with lost pieces of equipment is a daily occurence.
The responsibility of the person in such a case is usually limited to immediately letting the company know that they lost it (this is critical especially for things like RSA tokens, less so for phones/ipads etc.), and not to change any settings on the device they were explicitly told not to change (which may include not installing any SW). They may have to do more if they did stupid things like glue their password on the device or whatever (which would be a security breach in the first case).
The responsibility of the device provider (company, not the manufacturer) tends to be much more – like installing SW, making the right settings (and locking them down where possible) etc. etc.
The major problems aren’t actually iphones/ipads etc. but laptops, as you can have confidential information on them – but again, it’s really entirely up to the laptop provider to assess what can end up on the laptop and how it has to be protected.
“My understanding is iPads, at least, may be used to access both closed session and open session board materials. The closed session access would seem to make the loss of one of these iPads a security risk for the organization”
If a loss of an iPad alone can seriously compromise the security of a closed session at CalPERS, the problem is purely on CalPERS side as it means the access was not secured enough (short of Brown taping her passwords to the iPad or something similarly silly, but that would have nothing to do with the iPad loss).
The reporter should note that if this is what the article will be based upon, then either he, or CalPERS security IT will be laughed out of the town. I’m pretty damn sure that there’s a ton of IT security people in California who would have a great time picking it apart in social media.
That would also bode rather badly on any attempt to bring in the IT security inhouse.
Or maybe it’s ‘Classic CalPERS’ (to paraphrase Classic Dom) – if we’re incompetent externally, everyone can see it. Bring it inhouse, so we can be incompetent internally and pretend we’re good.
CalPERS staff can’t even indulge themselves in harassment of board refuseniks competently. Any large-ish organisation of any sort of maturity and sophistication (as I wrote that, I thought to myself how nice it would be if CalPERS acquire some of that, but never mind) has a written policy in place covering assets such as phones, tablets, laptops and so on.
For a start, remote wipe is an essential feature which must be set up and maintained on any device which can store private (organisational) data or access corporate data. CalPERS seem to ‘fess up that they do have this on their devices (it would be immediate grounds for state regulators to act if CalPERS failed to do this because it would be grossly negligent to not take reasonable steps to protect data). So there is zero — absolutely no — risk of data or CalPERS systems being compromised as a result of a lost or stolen device. Or, conversely, if there was a risk, it would be CalPERS’ fault there was a risk, not Board Member Brown’s.
Then the mobile device policy would, or should, state what would be deemed to be fair use of CalPERS’ assets by staff and the board members and what constitutes potential careless or not taking fair precautions to safeguard CalPERS’ property. My TBTF is fairly typical — you’re allowed to lose one device through your own mislaying it or theft every three years. Two losses in three years gets you a talking to from you manager. Three losses means you lose your privileges to have access to a company mobile device and you might be liable for disciplinary procedures if you were obviously being just careless.
If CalPERS staff are trying to engage in a smear campaign against Brown in the absence of having a written policy to cover the issue it’s their bad, not Brown’s
Indeed. As I wrote above, if this is the basis of the article, it will embarrass either the writer or CalPERS IT security staff, but not Brown.
What?!? Public records available to the public?!? Say it ain’t so!
And the SacBee finally launches their attack on Margaret Brown. It sounds like they want to use this non-incident to restrict Board members from accessing CalPERS private records from anywhere except at the CalPERS headquarters itself-
https://www.sacbee.com/news/politics-government/the-state-worker/article236585408.html
And another publication adds to the attack on Margaret Brown-
https://www.techwire.net/news/calpers-data-not-at-risk-from-lost-devices-agency-says.html